Introduction to HTTPS
HTTPS (Hypertext Transfer Protocol Secure) is a specialized version of HTTP (Hypertext Transfer Protocol) designed to ensure secure communication over the internet. It accomplishes this by utilizing advanced security protocols such as Transport Layer Security (TLS) or Secure Sockets Layer (SSL), which effectively safeguard data exchange between web servers and clients, including web browsers. To facilitate the transfer of data, HTTPS employs TCP as the transport layer, which ensures reliable and efficient delivery of information.
HTTPS network protocol stack
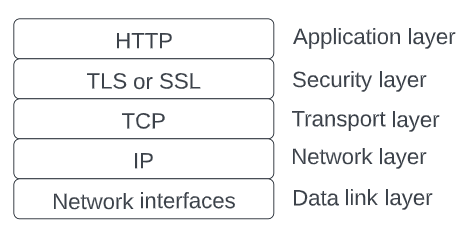
TLS version
In this particular instance, the TLS version 1.2 will be employed, as TLS 1.3 is generally regarded as an improvement upon TLS 1.2 rather than a fundamental departure from it. Hence, to maintain consistency and compatibility, TLS 1.2 is deemed suitable for this scenario.
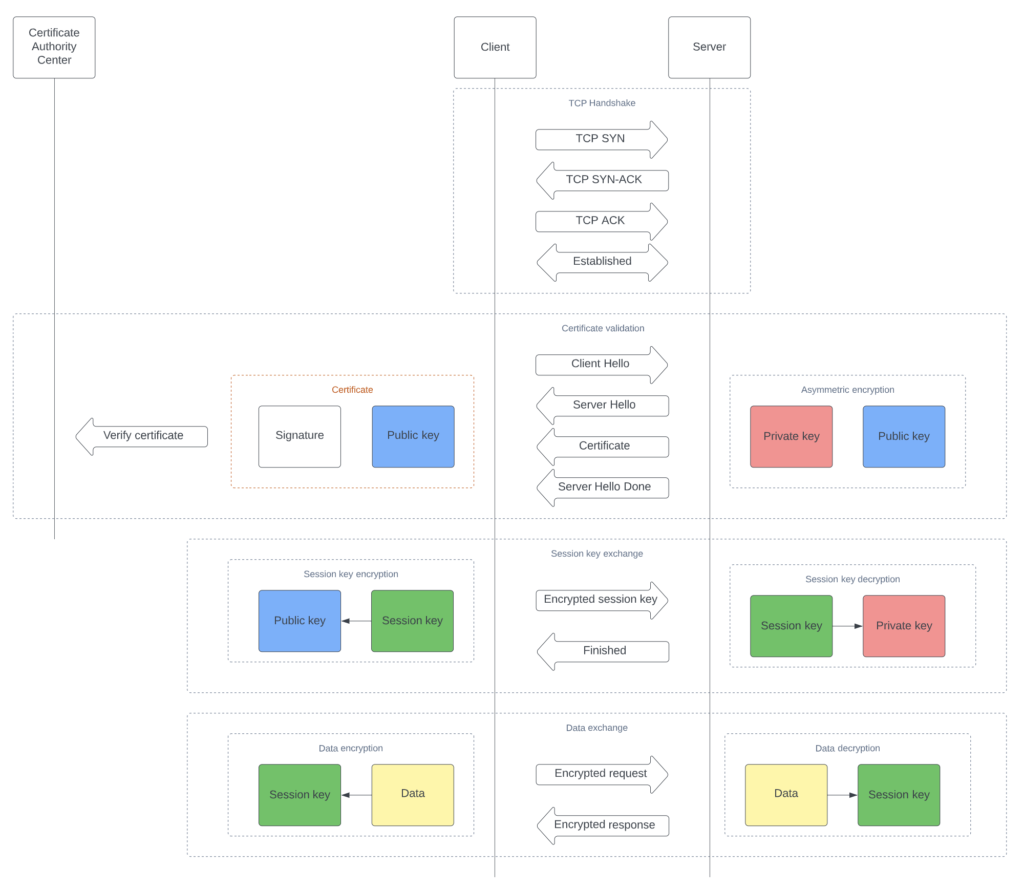
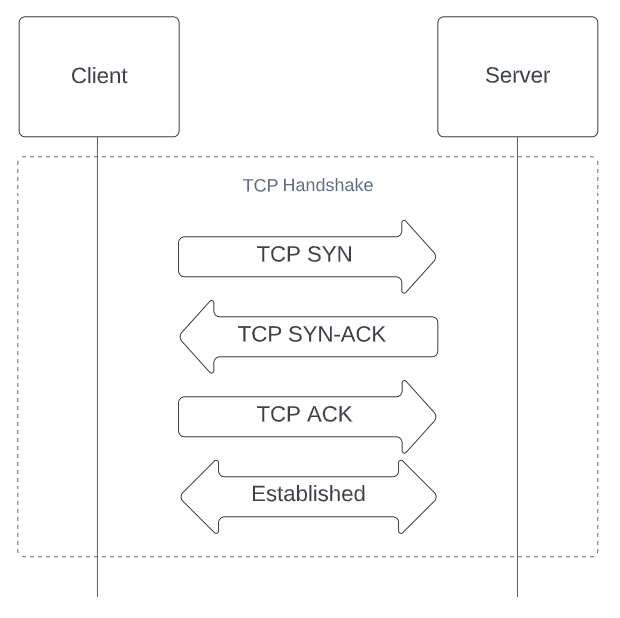
TCP Handshake
TCP is a type of protocol that prioritizes the establishment of a reliable and secure connection between two devices before transmitting any data. It achieves this by initiating a three-stage process, commonly known as a ‘3-way handshake’.
To commence the handshake, the client sends a synchronization request accompanied by a connection request.
The server then responds by sending an acknowledgement of the connection request, along with its synchronization request.
Lastly, the client confirms the connection, and the two devices are now connected and ready to exchange data.
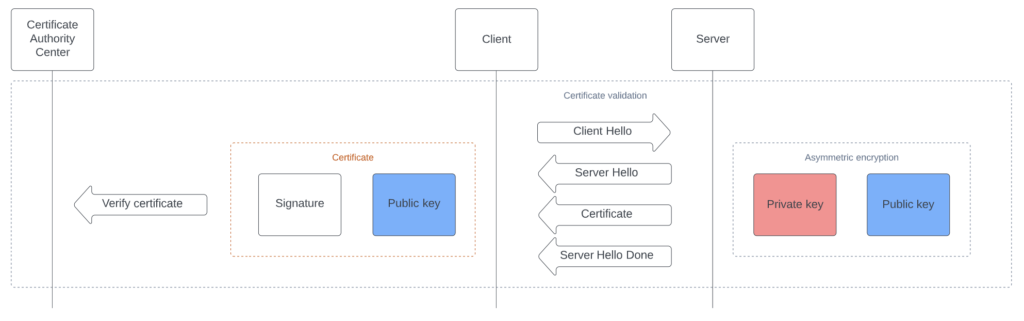
Certificate validation
- Client sends a ‘Hello’ message to the server to initiate the connection.
- Server responds by sending its certificate to the client.
- The client validates the certificate to ensure its authenticity before proceeding with the connection.
When establishing a secure connection, the client must validate the server’s digital certificate. The certificate validation process is critical as it helps to confirm that the client is interacting with the intended server and protects against potential man-in-the-middle attacks.
To validate the certificate, the client first receives the server’s digital certificate and proceeds to verify it. This involves checking that the certificate was issued by a trusted certification authority (CA), that it has not expired, and that the subject name or subject alternative name of the certificate matches the domain name of the server to which the client is trying to connect.
Once the certificate is deemed valid, the client can proceed with the connection, confident that they are communicating securely with the intended server.
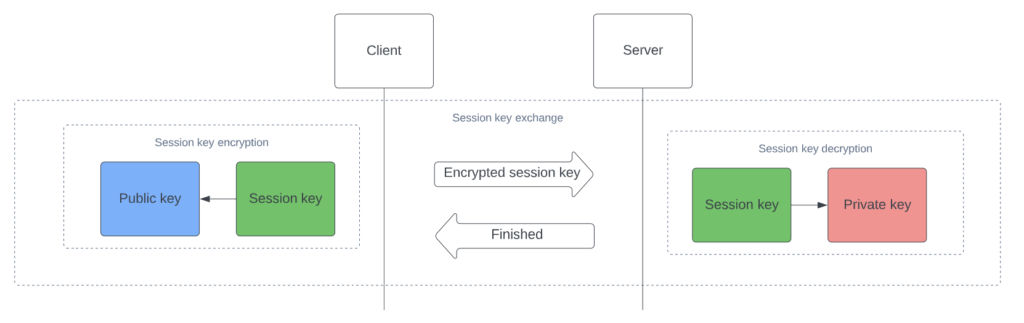
Session key exchange
- The client sends an encrypted session key
During the secure connection setup, the client extracts the public key from the server’s digital certificate and employs public key cryptography, also known as asymmetric encryption, to securely share the symmetric encryption key.
The client generates a symmetric encryption key, also known as a session key, which is used to encrypt and decrypt data transmitted between the client and server during the session. To ensure the confidentiality and integrity of the communication, the session key is encrypted using the server’s public key, which can only be decrypted using the corresponding private key held by the server.
While public key encryption provides a secure method for exchanging the session key, it can be computationally intensive for large amounts of data. Therefore, after the session key has been securely shared, symmetric encryption algorithms are used for primary data transmission, as they are generally faster and less computationally intensive than public key encryption algorithms.
Once the client has encrypted the session key using the server’s public key, it sends the encrypted session key to the server.
- The server sends a response about receiving the session key.
After receiving the encrypted session key from the client, the server decrypts it using its private key, which is securely stored and only accessible to the server. This allows both the client and server to have access to the same session key, which is used for encrypting and decrypting the transmitted data during the session.
Using the same session key for encryption and decryption ensures that the communication remains confidential and secure between the client and server. From this point forward, all data exchanged between the client and server is encrypted and decrypted using this session key.
Data exchange
- Sending Request
To initiate data exchange, the client encrypts its request and sends it to the server. The server receives the encrypted message and decrypts it using the session key.
- Receiving Response
Upon receiving the request, the server processes the request and sends back an encrypted response. The client then decrypts the response using the session key.

The full interaction diagram of HTTPS (Hypertext Transfer Protocol Secure)